You are here: Docs>Sheriff Web>UserGuides>SheriffCSMDocumentation>UserGuide>AssetManagement>AssetAdministration>ViewingAssetDetails (03 Jun 2022, SheriffCyberSecurity)Edit Attach
Up
Previous Next Sheriff CSM™ Viewing Asset Details To view asset details from the Asset List view, double-click a specific asset or click the magnifying glass (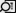 ) icon at the end of the row.
The Asset Details page looks similar to the following:
) icon at the end of the row.
The Asset Details page looks similar to the following:
 In Asset Details, on the left, you see the name and IP address, along with other fields that describe the particular asset.
In the middle, you see the status summary for your asset. (See Asset status circle color definitions for reference.)
At the bottom, you see a table area with tabs that correspond to the circles. Each tab contains a table with records, if present, for your asset. For example, in the figure shown, Host-172-16-1-10 has 37 vulnerabilities. On the Vulnerabilities tab (not shown), you see a table listing the 37 vulnerabilities, one by one. For details on what information each tab contains:
To check HIDS status
In Asset Details, on the left, you see the name and IP address, along with other fields that describe the particular asset.
In the middle, you see the status summary for your asset. (See Asset status circle color definitions for reference.)
At the bottom, you see a table area with tabs that correspond to the circles. Each tab contains a table with records, if present, for your asset. For example, in the figure shown, Host-172-16-1-10 has 37 vulnerabilities. On the Vulnerabilities tab (not shown), you see a table listing the 37 vulnerabilities, one by one. For details on what information each tab contains:
To check HIDS status
Previous Next Sheriff CSM™ Viewing Asset Details To view asset details from the Asset List view, double-click a specific asset or click the magnifying glass (
 In Asset Details, on the left, you see the name and IP address, along with other fields that describe the particular asset.
In the middle, you see the status summary for your asset. (See Asset status circle color definitions for reference.)
At the bottom, you see a table area with tabs that correspond to the circles. Each tab contains a table with records, if present, for your asset. For example, in the figure shown, Host-172-16-1-10 has 37 vulnerabilities. On the Vulnerabilities tab (not shown), you see a table listing the 37 vulnerabilities, one by one. For details on what information each tab contains:
In Asset Details, on the left, you see the name and IP address, along with other fields that describe the particular asset.
In the middle, you see the status summary for your asset. (See Asset status circle color definitions for reference.)
At the bottom, you see a table area with tabs that correspond to the circles. Each tab contains a table with records, if present, for your asset. For example, in the figure shown, Host-172-16-1-10 has 37 vulnerabilities. On the Vulnerabilities tab (not shown), you see a table listing the 37 vulnerabilities, one by one. For details on what information each tab contains:
Asset Details View Tab Description
| Tab | Information Shown |
|---|---|
| Vulnerabilities | Vulnerabilities related to this asset. |
| Alarms | Alarms related to this asset. |
| Events | Events related to this asset. |
| Software | Software installed on this asset. Use the Edit Software button to add, modify or delete software. |
| Services | Services available on this asset. Use the Edit Services button to add, modify or delete services. While in Edit Services, you can enable or disable availability monitoring for the service(s). |
| Plugins | Plugins enabled for this asset. Use the Edit Plugins button to enable or disable plugins for this asset. You can enable up to 10 plugins per asset and up to 100 plugins per Sheriff CSM Sensor (Deputy). |
| Properties | Properties specified for this asset. Use the Edit Properties button to add, modify or delete properties. |
| NetFlow | NetFlow information related to this asset. |
| Groups | Asset groups to which the asset belongs. Use the Add to Group button to add or remove the asset from an asset group. |
On the right side of the page, you see a list of Actions to perform on this asset. These consist of
- Edit
- Delete
- Run Asset Scan
- Run Vulnerability Scan
- Enable Availability Monitoring
- Disable Availability Monitoring
Environment Status Colors and Meetings for Assets
| Environment Status | Color | Meaning |
|---|---|---|
| HIDS | Green | An HIDS agent is deployed on this asset with status Active or Active/Local. |
| Yellow | A HIDS agent is deployed on this asset with status Disconnected. | |
| Red | A HIDS agent is deployed on this asset with status Never Connected. | |
| Gray | No HIDS agent is deployed on this asset. | |
| Automatic Asset Discovery | Green | All IP addresses associated with this asset are scheduled to be scanned. |
| Yellow | Some IP addresses associated with this asset are scheduled to be scanned. | |
| Red | No IP addresses associated with this asset is scheduled to be scanned. | |
| Vuln Scan Scheduled | Green | A vulnerability scan has been scheduled for this asset. |
| Red | No vulnerability scan has been scheduled for this asset. |
-
Click HIDS.
This takes you to Environment > Detection > HIDS > Overview, where you see a list of HIDS agents along with their status.
-
Click Automatic Asset Discovery.
This takes you to Environment > Assets & Groups > Scheduled Scan, where you can schedule an asset discovery scan. See Scheduling an Asset Discovery Scan.
-
Click Vuln Scan Scheduled.
This takes you to Environment > Vulnerabilities > Scan Jobs, where you see a list of vulnerability scan jobs.
-
Click See Network Activity.
This takes you to Environment > NetFlow > Details, with the IP address of the asset set as either the source or destination.
- Click the message.
Edit | Attach | Print version | History: r13 < r12 < r11 < r10 | Backlinks | View wiki text | Edit wiki text | More topic actions
Topic revision: r13 - 03 Jun 2022, SheriffCyberSecurity
Copyright 2020 Sheriff Cyber Security, LLC. All rights reserved.


