You are here: Docs>Sheriff Web>UserGuides>SheriffCSMDocumentation>UserGuide>EventManagement>ReviewSecurityEvents>ReviewEventDetails (07 Mar 2022, SheriffCyberSecurity)Edit Attach
Up
Previous Next Sheriff CSM™ Review Event Details Event Details identifies all information Sheriff CSM collected about this event. It also displays the number of indicators involved, when the event relates to an Open Threat Exchange® (OTX™) pulse, and the IP reputation-calculated reliability and risk level data.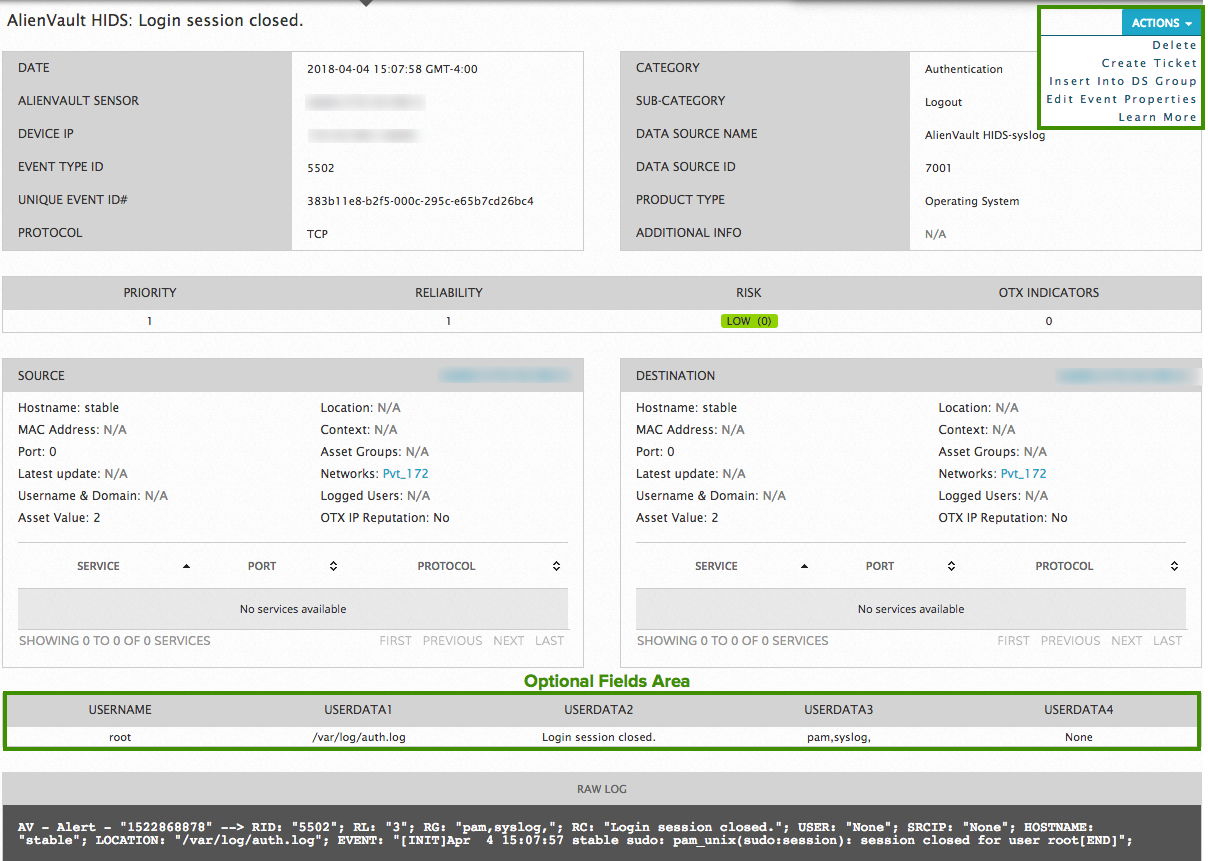 Event Detail Fields (order as appeared on the web UI)
Event Detail Fields (order as appeared on the web UI)
When you see N/A displayed for a certain field, it means that Sheriff CSM has no related data in the event log or the asset inventory.
When event data derives from a log or the asset inventory, some of the fields below appear after Service, Port, and Protocol and above the Raw Log data. (See screenshot above.) Otherwise, these fields do not display.
Optional Event Fields
There are some actions you can perform directly from the event details page.
Sheriff Vigilante Limitations: The Sheriff CSM SIEM engine has more diverse capabilities in handling events due to its built-in correlation abilities and graph-based analytics.
Previous Next Sheriff CSM™ Review Event Details Event Details identifies all information Sheriff CSM collected about this event. It also displays the number of indicators involved, when the event relates to an Open Threat Exchange® (OTX™) pulse, and the IP reputation-calculated reliability and risk level data.
 Event Detail Fields (order as appeared on the web UI)
Event Detail Fields (order as appeared on the web UI)
| Fields | Description | |
|---|---|---|
| Date | Date and time of the event. | |
| SheriffSensor (Deputy) | Sensor that processed the event. | |
| Device IP | IP address of the Sheriff CSM Sensor that processed the event. | |
| Event Type ID | ID assigned by Sheriff CSM to identify the event type. | |
| Unique Event ID# | Unique ID number assigned to the event by Sheriff CSM. | |
| Protocol | Protocol used for the source/destination of the event, for example, TCP IP. | |
| Category | Event taxonomy for the event, for example, Authentication or Exploit. | |
| Sub-Category | Subcategory of the event taxonomy type listed under Category. For example, this would be Denial of Service, if the category were Exploit. | |
| Data Source Name | Name of the external application or device that produced the event. | |
| Data Source ID | ID associated with the external application or device that produced the event. | |
| Product Type | Product type of the event taxonomy, for example, Operating System or Server. Note: Events with IP Reputation-related data have product types; OTX pulses do not. | |
| Additional Info | If the event were generated by a suspicious URL, for example, this field would state URL. When present, these URLs provide additional background information and references about the components associated with the event. | |
| Priority | Priority ranking, based on value of the event type. Each event type has a priority value, used in risk calculation. | |
| Reliability | Reliability ranking, based on the reliability value of the event type. Each event type has a reliability value, which is used in risk calculation. | |
| Risk | Risk level of the event: Low = 0, Medium = 1, High > 1 Note: Risk calculation is based on this formula: Asset Value * Event Reliability * Event Priority / 25 = Risk If Asset Value = 3, Reliability = 2 and Priority = 2, the risk would be 3 * 2 * 2 / 25 = 0.48 (rounded down to 0) Therefore, Risk is Low | |
| OTX Indicators | Number of indicators associated with an IP Reputation or OTX pulse event. | |
| Source / Destination | IP addresses and hostname for the source and destination, respectively, of the event. If the host is an asset, you can right-click it to go to the Asset Details page for information. Right-clicking the IP address displays a menu from which you can select information about the IP, such as all events originating from that host or all events for which the IP is the destination. | |
| Hostname | Hostname of the event source/destination. If the source or destination hostname for an event is within your asset inventory, this field contains a value. You can click it to go to the Asset Details page for more information. | |
| MAC Address | Media Access Control (MAC) of the host for the event, if known. | |
| Port | External or internal asset source/destination port for the event. | |
| Latest Update | The last time Sheriff CSM updated the asset properties. | |
| Username & Domain | Username and domain associated with the asset that generated the event. | |
| Asset Value | Asset value of the asset source/destination if within your asset inventory. | |
| Location | If the host country of origin is known, displays the national flag of the event source or destination. | |
| Context | If the asset belongs to a user-defined group of entities, Sheriff CSM displays the contexts. | |
| Asset Groups | When the host for the event source/destination is an asset belonging to one or more of your asset groups, this field lists the asset group name or names. You can click the field to go to the Asset Details page for more information. | |
| Networks | When the host for the event source/destination is an asset belonging to one or more of your networks, this field lists the networks. You can click the field to go to the Network Group Details page for more information. | |
| Logged Users | A list of any users who have been active on the asset, as detected by the asset scan, for example, with the username and user privilege (such as admin). | |
| OTX IP Reputation | (Yes/No) Whether or not IP Reputation identifies the IP address as suspicious. | |
| Service | List of services or applications detected on the source/destination port. | |
| Port | Port used by the service or application. | |
| Protocol | Protocol used by the service or application. | |
| Raw Log | Raw log details of the event. | |
| Fields | Description |
|---|---|
| Filename | Name of file associated with the event. |
| Username | The username associated with the event. |
| Password | The password associated with the event. |
| Userdata 1-9 | User-created log fields. |
| Payload | Payload of the event. |
| Rule Detection | Sheriff NIDS rule used to detect the event. |
Actions on Event Details
| Actions | Description |
|---|---|
| Delete | Delete the event. |
| Create Ticket | Create a ticket in Sheriff CSM based on the event. |
| Insert Into DS Group | Add this event type into an existing data source group. |
| Edit Event Properties | Change the default priority and/or reliability value of this event type so that the calculated risk will differ. Changes will apply to future events. |
| Learn More | Launches the Knowledge Base information for this event. |
Edit | Attach | Print version | History: r15 < r14 < r13 < r12 | Backlinks | View wiki text | Edit wiki text | More topic actions
Topic revision: r15 - 07 Mar 2022, SheriffCyberSecurity
Copyright 2020 Sheriff Cyber Security, LLC. All rights reserved.
