You are here: Docs>Sheriff Web>UserGuides>SheriffCSMDocumentation>UserGuide>EventManagement>ReviewSecurityEvents>DefineAdvancedSearchCriteriaForSecurityEvents (27 Jan 2022, SheriffCyberSecurity)Edit Attach
Up
Previous Next Sheriff CSM™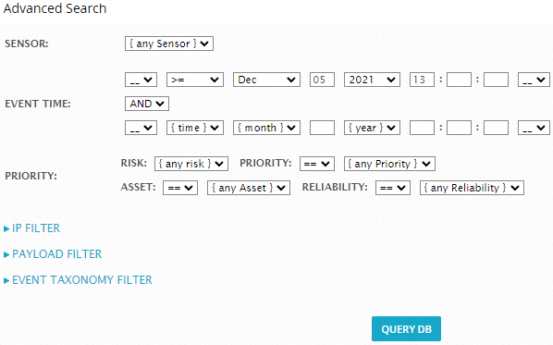 This new window allows for detailed search on Event Time, Priority, IP, Payload, or Event Taxonomy. Click Query DB to start the search after you have specified the criteria.
This new window allows for detailed search on Event Time, Priority, IP, Payload, or Event Taxonomy. Click Query DB to start the search after you have specified the criteria.
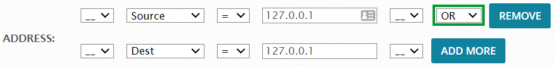
 Click Add More to specify additional IP addresses. You can select "AND" or "OR" to combine them:
Click Add More to specify additional IP addresses. You can select "AND" or "OR" to combine them:
 If you want to add a port number for TCP or UDF, click the corresponding button to display the options. For example
If you want to add a port number for TCP or UDF, click the corresponding button to display the options. For example
 Click Add More to specify additional port numbers. You can select "AND" or "OR" to combine them.
Click Add More to specify additional port numbers. You can select "AND" or "OR" to combine them.
 Using the encoding and Convert To drop-down, you can convert the search string from ASCII to HEX, for example, should it be required.
Click Add More to specify additional payload criteria. You can select "AND" or "OR" to combine them.
Example:
The example below specifies criteria to search for events that contain the string "testmyids.com" OR "google.com" in the payload:
Important: Do not include quotes when entering the search strings.
Using the encoding and Convert To drop-down, you can convert the search string from ASCII to HEX, for example, should it be required.
Click Add More to specify additional payload criteria. You can select "AND" or "OR" to combine them.
Example:
The example below specifies criteria to search for events that contain the string "testmyids.com" OR "google.com" in the payload:
Important: Do not include quotes when entering the search strings.
 For details on product type and event category, see Product Types and Categories.
Sheriff Vigilante Limitations: The Sheriff CSM SIEM engine has more diverse capabilities in handling events due to its built-in correlation abilities and graph-based analytics.
For details on product type and event category, see Product Types and Categories.
Sheriff Vigilante Limitations: The Sheriff CSM SIEM engine has more diverse capabilities in handling events due to its built-in correlation abilities and graph-based analytics.
Previous Next Sheriff CSM™
Define Advanced Search Criteria for Security Events (SIEM)
This topic describes how to define advanced search criteria when performing a search on Analysis > Security Events (SIEM). When you click Advanced Search, the following window opens: This new window allows for detailed search on Event Time, Priority, IP, Payload, or Event Taxonomy. Click Query DB to start the search after you have specified the criteria.
This new window allows for detailed search on Event Time, Priority, IP, Payload, or Event Taxonomy. Click Query DB to start the search after you have specified the criteria.
Sensor (Deputy)
This filter allows you to select a deployed Sheriff CSM Sensor from the list.Event Time
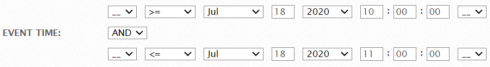
This option allows for fine grain filtering for events that occurred at a specific date and time. Use the "time" drop-down to select greater than (>), less than (<), or not equal (=) operators. You can use a wildcard (*) when specifying the time of the event. Select the "AND" or "OR" operator if you need to limit the search within two time settings. Example: In the screenshot below, the selections made will search for events that occurred after (>=) 10:00:00 AND before (<=) 11:00:00 on the 12th of July 2020, reducing the time frame to one particular hour on one specific date.
Priority
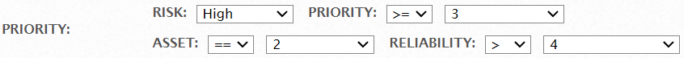
This filter allows you to specify the Asset Value, Event Reliability, and Event Priority individually. Example: In the screenshot below, the options specified will search for events with a High Risk, a Priority of 3 or more, an Asset value of 2, and a Reliability greater than 4.IP Filter
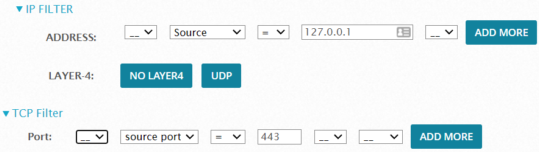
Click IP Filter to display the options, which allow you to specify Layer 3 IP addresses and Layer 4 TCP or UDP protocols. Click Add More to specify additional IP addresses. You can select "AND" or "OR" to combine them:
Click Add More to specify additional IP addresses. You can select "AND" or "OR" to combine them:
 If you want to add a port number for TCP or UDF, click the corresponding button to display the options. For example
If you want to add a port number for TCP or UDF, click the corresponding button to display the options. For example
 Click Add More to specify additional port numbers. You can select "AND" or "OR" to combine them.
Click Add More to specify additional port numbers. You can select "AND" or "OR" to combine them.
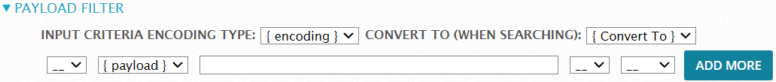
Payload Filter
Click Payload Filter to display the options, which allow you to specify what you want to search in the payload of an event. Using the encoding and Convert To drop-down, you can convert the search string from ASCII to HEX, for example, should it be required.
Click Add More to specify additional payload criteria. You can select "AND" or "OR" to combine them.
Example:
The example below specifies criteria to search for events that contain the string "testmyids.com" OR "google.com" in the payload:
Important: Do not include quotes when entering the search strings.
Using the encoding and Convert To drop-down, you can convert the search string from ASCII to HEX, for example, should it be required.
Click Add More to specify additional payload criteria. You can select "AND" or "OR" to combine them.
Example:
The example below specifies criteria to search for events that contain the string "testmyids.com" OR "google.com" in the payload:
Important: Do not include quotes when entering the search strings.
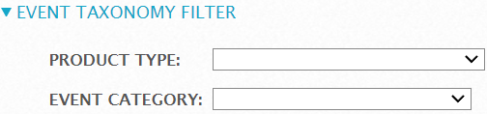
Event Taxonomy Filter
Event Taxonomy Filter allows you to search for events using event taxonomy. For details on product type and event category, see Product Types and Categories.
Sheriff Vigilante Limitations: The Sheriff CSM SIEM engine has more diverse capabilities in handling events due to its built-in correlation abilities and graph-based analytics.
For details on product type and event category, see Product Types and Categories.
Sheriff Vigilante Limitations: The Sheriff CSM SIEM engine has more diverse capabilities in handling events due to its built-in correlation abilities and graph-based analytics. Edit | Attach | Print version | History: r14 < r13 < r12 < r11 | Backlinks | View wiki text | Edit wiki text | More topic actions
Topic revision: r14 - 27 Jan 2022, SheriffCyberSecurity
Copyright 2020 Sheriff Cyber Security, LLC. All rights reserved.
