Previous Next Sheriff CSM™ Working with Sheriff HIDS Rules Sheriff HIDS expands from the open source project, OSSEC, by providing additional rules that are essential to identifying HIDS issues. The table below lists all the Sheriff-specific rules that Sheriff CSM provides out of the box. Sheriff HIDS Rules
| Rule File Name | Rules Purpose | Enabled by Default | Rule File Dependency | Windows Event ID Matched |
|---|---|---|---|---|
| sheriff-apache_rules.xml | Rules for Apache HTTP Server | No | apache_rules.xml | N/A |
| sheriff-directory-service_rules.xml | Detect changes of directory service objects in Active Directory on Windows | Yes | msauth_rules.xml | 5136, 5137, 5138, 5139, 5141 |
| sheriff-domain_rules.xml | Detect changes in the Domain Admins group on Windows | Yes | msauth_rules.xml | SID: S-1-5-21 domain 512, 518, and 519 |
| sheriff-linux-USB_rules.xml | Detect new USB devices on Linux | No | None | N/A |
| sheriff-linux-pam_rules.xml | Detect SSHD authentication on Linux | No | None | N/A |
| sheriff-mssql_rules.xml | Rules for Microsoft SQL Server | No | msauth_rules.xml | 14151, 18265, 33205 |
| sheriff-network-login-failure_rules.xml | Detect failed logon attempts on Windows | No | msauth_rules.xml | 46251 |
| sheriff-sam-express_rules.xml | Rules for SAM (SafeNet Authentication Manager) Express | No | msauth_rules.xml | N/A |
| sheriff-web-access_rules.xml | Rules to supplement the default web access rules | No | web_rules.xml | N/A |
| sheriff-windows-ADFS-servers_rules.xml | Rules for Active Directory Federation Services on Windows | No | msauth_rules.xml | 1102 |
| sheriff-windows-DHCP_rules.xml | Detect DHCP lease actions on Windows | No | ms_dhcp_rules.xml | DHCP server event 10, 11, 12, 13, 16, 17, 18, 20, 21, 23, 30, 32 |
| sheriff-windows-FIM_rules.xml | Detect file changes on Windows | Yes | msauth_rules.xml | 4659 |
| sheriff-windows-USB_rules.xml | Detect new USB devices on Windows | Yes | ossec_rules.xml | N/A |
| sheriff-windows-access_rules.xml | Detect Object Access issues on Windows | No | msauth_rules.xml | 4656, 4662, 4673, 4674 |
| sheriff-windows-account-security_rules.xml | Detect account activities on Windows | No | msauth_rules.xml | 4720, 4722, 4725, 4726, 4738, 4781 |
| sheriff-windows-applocker_rules.xml | Detect AppLocker activities on Windows | No | msauth_rules.xml | 8002, 8003, 8004, 8005, 8006, 8007 |
| sheriff-windows-capacity_rules.xml | Detect capacity issues on Windows | No | msauth_rules.xml | 2013 |
| sheriff-windows-defender_rules.xml | Rules for Windows Defender | No | msauth_rules.xml, ms-se_rules.xml | 1000, 1001, 1116, 1117, 5007 |
| sheriff-windows-filtering_rules.xml | Rules for Windows Filtering Platform (WFP) | No | msauth_rules.xml | 5152 |
| sheriff-windows-group-changes_rules.xml | Detect Security group changes in Active Directory on Windows | No | msauth_rules.xml | 4735, 4737, 4755 |
| sheriff-windows-logon-logoff_rules.xml | Detect machine log on/off attempts on Windows | Yes | msauth_rules.xml | N/A |
| sheriff-windows-password-change-rules.xml | Detect password change attempts on Windows | No | msauth_rules.xml | 4723, 4724 |
| sheriff-windows-powershell_rules.xml | Rules for Windows PowerShellcommands | No | msauth_rules.xml | 800 |
| sheriff-windows-process_rules.xml | Detect new processes on Windows | No | msauth_rules.xml | 4688, 4689 |
| sheriff-windows-service-control-manager_rules.xml | Rules for Service Control Manager (Windows) | No | msauth_rules.xml | 7036, 7045 |
| sheriff-windows-shutdown_rules.xml | Detect power off attempts on Windows | No | msauth_rules.xml | 1074 |
| sheriff-windows-workstation-logon-logoff_rules.xml | Detect user logon/off attempts on Windows | Yes | msauth_rules.xml | 528, 540, 672, 673, 4624, 4672, 4768, 4769, 4771 |
| local_rules.xml | A file to hold user-defined HIDS rules. it contains a sample rule initially. | Yes | None by default | N/A |
 You can enable more rules based on your business needs. See Enabling / Disabling Sheriff HIDS Rules.
Additionally, you can edit existing rules or create your own so that they work better in your environment. See Editing / Creating Custom Rules for Sheriff HIDS.
You can enable more rules based on your business needs. See Enabling / Disabling Sheriff HIDS Rules.
Additionally, you can edit existing rules or create your own so that they work better in your environment. See Editing / Creating Custom Rules for Sheriff HIDS.
Enabling / Disabling Sheriff HIDS Rules
Before deciding whether to enable or disable an Sheriff HIDS rule, you will want to understand what the rule does first. Sheriff CSM allows you to view the entire rule file from the web UI. Note: Sheriff HIDS rules are read-only. You cannot change them. To view a HIDS rule file-
Go to Environment > Detection > Edit Rules.
-
Select the rule file from the drop-down list.
- Click the plus (+) sign to extend the nodes, or click a node to display the details in the right column.
-
Alternatively, click the Rule Editor tab to see the rule file in XML format.
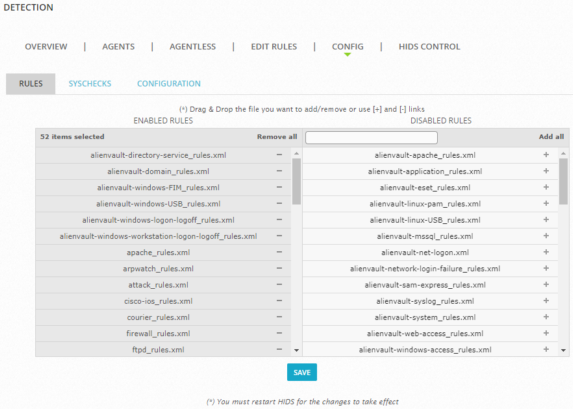
- Go to Environment > Detection > Config > Rules.
-
To enable a rule, type the name of the rule in the search box.
The number of available rules reduces as you type and Sheriff CSM finds the match.
-
To locate the rule, either drag the file to the left column or click the plus (+) sign next to the rule.
-
To disable a rule, locate the file in the left column. Either drag the file to the right column or click the minus (-) sign next to the rule.
- Click Save.
-
You must restart the HIDS Service for the changes to take effect:
- On the same page, click the HIDS Control tab, and then click Restart on the resulting page.
Editing / Creating Custom Rules for Sheriff HIDS
You are not allowed to change any of the Sheriff HIDS rules, but you can create your own rules to detect HIDS issues in your environment. Sheriff recommends that you put your rules in thelocal_rules.xml file, which is enabled by default and loaded at last so that it is not overwritten by the other rule files. You can add or remove rules from local_rules.xml in the web UI.
To create or modify a custom HIDS rule - Go to Environment > Detection > Edit Rules.
-
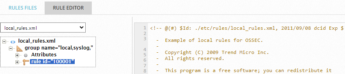
Select local_rules.xml from the drop-down list.
-
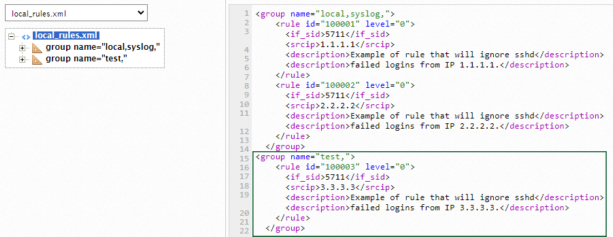
Click group name="local,syslog," to display the details in the right column.
A sample rule with id 100001 displays.
-
Click the clone rule icon (
 ) to clone the sample rule.
) to clone the sample rule.Another rule with rule id 100001 displays.
-
Click Save.
Note: Save your new rule in order to make changes to it.
-
Click the edit rule icon (
 ) next to the newly created rule.
) next to the newly created rule.The details of the rule display.
-
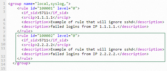
Change the id so that it is unique.
Important: A valid custom rule ID for Sheriff HIDS is between 190,000 and 199,999. Sheriff reserves other ranges for its internal usage.
-
Change the other attributes as needed. Use the add icon (
 ) to add an attribute or a node. Use the delete icon (
) to add an attribute or a node. Use the delete icon ( ) to remove an attribute or a node.
) to remove an attribute or a node.In the example below, we have changed the rule id to 100002 and srcip to 2.2.2.2. We have updated the description as well.
- If you need to add an attribute for any of the nodes, click the show icon (
 ) to display the attributes for that node.
) to display the attributes for that node.
-
Alternatively, if you prefer to use the XML format, click the Rule Editor tab and enter your rule directly.
- Click Save after you have made all the changes.
-
You must restart the HIDS Service for the changes to take effect:
- On the same page, click the HIDS Control tab, and then click Restart on the resulting page.
- On the same page, click the HIDS Control tab, and then click Restart on the resulting page.
 Important: Do not add a group without a rule in it. Sheriff HIDS will not restart with an empty group in local_rules.xml.
Sheriff Vigilante Limitations: Both Sheriff Vigilante and the Sheriff CSM HIDS decoders are fully featured, with all of their information coming from the Plugin Feed Updates that Sheriff CSM and Sheriff Vigilante provide. However, Sheriff Vigilante lacks the depth of NIDS information that is provided to Sheriff CSM through the Threat Intelligence Updates.
Important: Do not add a group without a rule in it. Sheriff HIDS will not restart with an empty group in local_rules.xml.
Sheriff Vigilante Limitations: Both Sheriff Vigilante and the Sheriff CSM HIDS decoders are fully featured, with all of their information coming from the Plugin Feed Updates that Sheriff CSM and Sheriff Vigilante provide. However, Sheriff Vigilante lacks the depth of NIDS information that is provided to Sheriff CSM through the Threat Intelligence Updates.
Topic revision: 03 Oct 2021, SheriffCyberSecurity