Previous Next Sheriff CSM™ Agentless Monitoring Sheriff HIDS allows you to run integrity checking without agents installed on hosts, network devices, routers, firewalls, or switches. Agentless monitoring detects checksum changes in files or runs diffs to shows what exactly has changed.
Prerequisites
Before enabling agentless monitoring, make sure you have done the following:- Open the SSH daemon on your device listening on TCP port 22.
- Set up firewall rules to allow SSH traffic between Sheriff CSM and your device.
Enabling Agentless Monitoring
To enable agentless monitoring-
Go to Environment > Detection > Agentless.
-
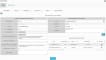
To add a new host you want to monitor, click New towards the right.
- Fill out the Agentless Data Configuration information on the left.
-
Fill out the Monitoring Entries Options information on the right, then click Add.
Monitoring entries optionsFields Values Explanation Supported Arguments by Type Type Integrity Check BSD Performs BSD-specific integrity checking on folders. List of folders to monitor. For example: -
/bin -
/etc/sbin
Integrity Check Linux Performs Linux-specific integrity checking on folders. List of folders to monitor. For example: -
/bin -
/etc/sbin
Generic Command Diff Runs a list of commands you specify and creates an event if output changes. List of commands whose output you want to compare. For example: -
ls -la /etc -
cat /etc/passwd
Cisco Config Check Checks device configuration using Cisco‑compatible commands. Leave it empty. Foundry Config Check Checks device configuration using Foundry-compatible commands. Leave it empty. ASA FWSMconfig Check Checks device configuration using Cisco ASA-compatible commands. Leave it empty. Frequency (Default) 86400 How often Sheriff HIDS runs the checks, in seconds. N/A Arguments /bin/etc/sbin Arguments that correspond to the type of check you select. See the Supported Arguments by Type column in this table.
N/A Important: Sheriff CSM can only process one argument for every entry. If you need to run multiple commands, put them in separate entries. The added entries appear in Monitoring Entries Added.
-
-
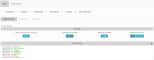
Click Update.
-
To apply your changes immediately, click HIDS Control, and then Restart.
This starts the agentless service in the Sheriff HIDS.
Verifying the Agentless Deployment on Sheriff CSM
You can verify that you have successfully deployed the agentless monitoring in the following ways:-
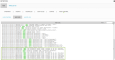
On Environment > Detection > Agentless, the status of the host displays a green checkmark, and the Agentless Status: displays Running.
-
On Environment > Detection > HIDS Control, make sure that you see "Agentless is running" in green.
-
On Environment > Detection > HIDS Control > HIDS Log, make sure that you see the periodic checks performed.
-
On Analysis > Security Events (SIEM), make sure that you see events coming from the monitored host or device.
Sheriff Vigilante Limitations: Both Sheriff Vigilante and the Sheriff CSM HIDS decoders are fully featured, with all of their information coming from the Plugin Feed Updates that Sheriff CSM and Sheriff Vigilante provide. However, Sheriff Vigilante lacks the depth of NIDS information that is provided to Sheriff CSM through the Threat Intelligence Updates.