Previous Next
Sheriff CSM™
Using OTX in Sheriff CSM
When you sign up for and connect your Open Threat Exchange® (OTX™) account to your Sheriff CSM instance, it configures Sheriff CSM to receive raw pulse data and other IP reputation information. Note: Reputation data is updated separately from OTX pulse information. Sheriff CSM then correlates that data with incoming events, alerting you to OTX pulse and IP Reputation-related security events/alarms when it detects IoCs interacting with assets in your environment. Such interactions might consist of malicious IPs communicating with systems, malware detected in your network, or outbound communication with command-and-control (C&C) servers. Connecting OTX to Sheriff CSM helps manage risks and threats in the following ways:-
Sheriff CSM detects threat updates every 30 minutes for all pulses to which you subscribe, either directly or through subscriptions to other OTX users.
- You receive updates on your subscribed pulses by email, either individually as they occur or in digest mode.
-
You can review OTX pulses about related threat vectors in Sheriff CSM.
-
As soon as you log into Sheriff CSM, you can see which pulses are most active in your environment by looking at the Sheriff CSM Dashboards Overview.
-
Sheriff CSM checks OTX pulses against all NIDS events. It generates an alarm when a malicious IP address communicates with any of your assets, or when some of the other IoCs, including CIDR (IPv4 only), domain, and hostname, are detected in your network.
-
In a distributed environment, the Sheriff CSM Server replicates the OTX pulses to the connected Sheriff CSM Deputies through TCP port 6380. This replication is read-only so that the copy on the Sheriff CSM Server remains intact.
Note: When a Sheriff CSM Deputy is added to the Sheriff CSM Server, a firewall rule is created to allow OTX traffic going through TCP port 6380. When the Deputy is removed, the firewall rule is deleted. The same mechanism is used in a high availability (HA) deployment to replicate OTX pulses between nodes.
OTX IP Reputation Data Correlated with Events
Sheriff CSM maintains an IP reputation list that stores data it receives from OTX about public IP addresses involved in malicious or other suspect activities. Whenever an event has its source or destination IP addresses listed in the IP Reputation list, reputation data will be added to the data stored for the event. This allows Sheriff CSM to support some additional features like reprioritization of events and alarms depending on the IP of the hosts involved. The IP reputation list maintained by Sheriff CSM is stored on the Sheriff CSM Server in the/etc/vigilante/server/reputation.data file. Activity, Reliability, and Priority values provided by OTX are saved with event information for those events having reputation data for either source or destination IP addresses.
The main purpose of the IP reputation list is to provide a list of known or potentially dangerous IP addresses. If any alarm or event is generated by the action of a listed dangerous IP address, then this event will have a smaller probability of being a false positive. This also allows for the recalculation of event/alarm risk depending on its' "IP Reliability" and "IP Priority" values.
Note: Reputation events are anonymized and submitted to the AlienVault OTX service for those customers who enable that capability in Sheriff CSM. With the feedback received from customer systems and all the other sources Sheriff uses, the IP Reputation values are updated before being redistributed to customers.
Displaying Alarms and Events Based on OTX Pulse and IP Reputation
The Sheriff CSM Alarm and Security Events (SIEM) web UI each provide methods of searching for and filtering alarm and security events based on OTX pulse and IP Reputation information. For each event, the database stores associated information on the source and destination IP address provided by OTX, in addition to the activity reported in the event, for example, spamming, phishing, scanning, malware distribution, and so on.Viewing OTX Alarms
Different from the way other alarms are processed, Sheriff CSM generates an alarm whenever it detects even one event associated with an OTX pulse. Alarm correlation begins at that point and proceeds for a period of 24 hours. During this time, Sheriff CSM adds any new events related to that pulse to the same alarm. If any new events related to the pulse occur after that 24-hour period, Sheriff CSM generates a second alarm and a new correlation period begins. As an exception to this rule, should an event contain data on record with OTX IP Reputation information, Sheriff CSM correlates the alarm, using its standard directive taxonomy. Note: If an OTX pulse is creating too much noise and generating too many false positive alarms, you can always just unsubscribe from the pulse. Sheriff CSM does not offer a filter for IP Reputation-based alarms. However, you can view these within the Alarms list, where they occur.Searching, Filtering, and Viewing Events
From the Sheriff CSM Security Events (SIEM) page, you can search for and filter events based on whether OTX pulses exist for source or destination IP addresses, as well as the severity of different IP Reputation scores. The following screen shot highlights fields in which you can select OTX pulse and IP Reputation search/filter options.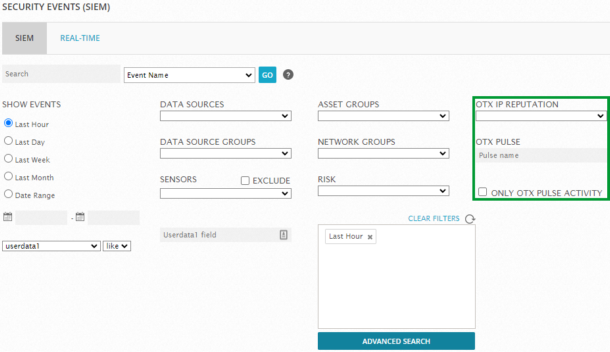 Selecting the OTX IP Reputation field opens a menu list in which you can choose to display only events that meet or exceed a specific IP Reputation severity level.
Selecting the OTX IP Reputation field opens a menu list in which you can choose to display only events that meet or exceed a specific IP Reputation severity level.
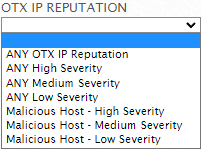 The Low, Medium, and High severity levels take in account the OTX IP priority values of both the source and destination IP addresses included in events, based on the following rules:
The Low, Medium, and High severity levels take in account the OTX IP priority values of both the source and destination IP addresses included in events, based on the following rules: -
Low Severity — returns events that have a source or destination IP priority of 0, 1, or 2.
-
Medium Severity — returns events that have a source or destination IP priority of 3, 4, 5, or 6.
-
High Severity — returns events that have a source or destination IP priority greater than 6.
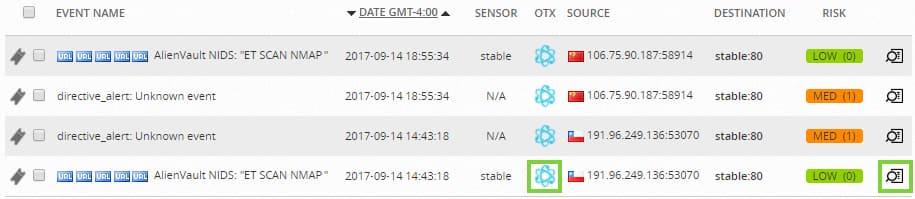 In this example, the event list display shows events in which the Any OTX IP Reputation filter option was selected. The OTX field displays the blue
In this example, the event list display shows events in which the Any OTX IP Reputation filter option was selected. The OTX field displays the blue Displaying OTX Pulse and IP Reputation Information in Event and Alarm Displays
In the SIEM Events list, you can click the orange or blue OTX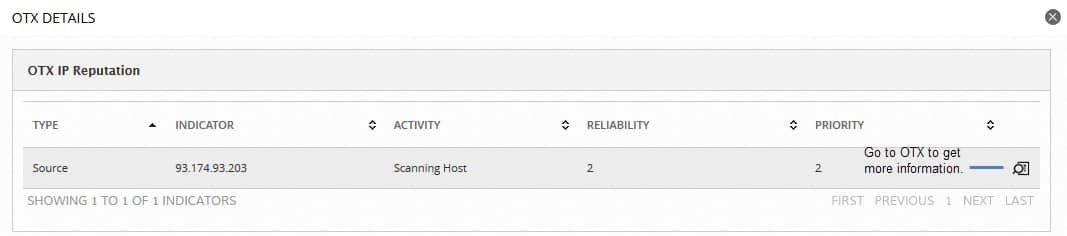 OTX Details — IP Reputation
OTX Details — IP Reputation
| Field | Description |
|---|---|
| Type | Tells you whether the indicator is the source or the destination of the event. |
| Indicator | IP address or hostname of the event source. |
| Activity | Type of malicious activity identified, for example, a scanning host. |
| Reliability | OTX IP reliability score, with values ranging from 1 to 10; 10 being the highest reliability. |
| Priority | OTX IP priority score, with values ranging from 1 to 10; 10 being the highest priority. |
| Magnifying glass icon | Clicking on the magnifying glass icon takes you to OTX to learn more about the indicator. |
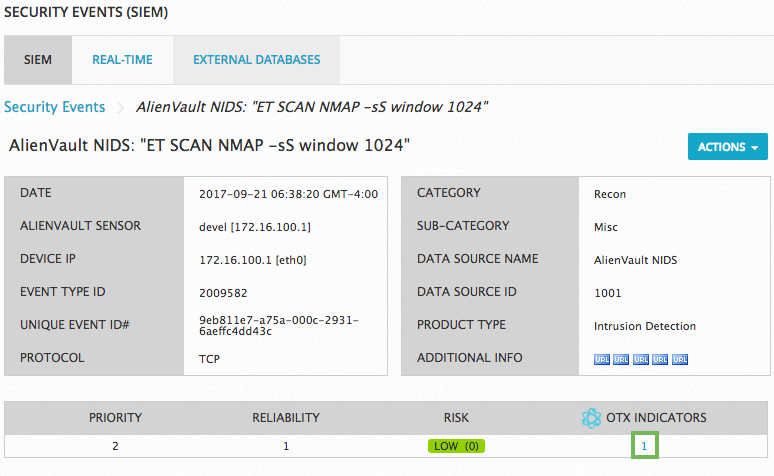 From this display, you can click the number in blue under OTX Indicators to get more OTX details about an indicator.
In addition to other navigation options, in both Alarm and SIEM Event list views, you can right-click on Source and Destination IP addresses or host names, which will display a popup menu of available actions you can take corresponding to a specific IP address or host name.
From this display, you can click the number in blue under OTX Indicators to get more OTX details about an indicator.
In addition to other navigation options, in both Alarm and SIEM Event list views, you can right-click on Source and Destination IP addresses or host names, which will display a popup menu of available actions you can take corresponding to a specific IP address or host name.
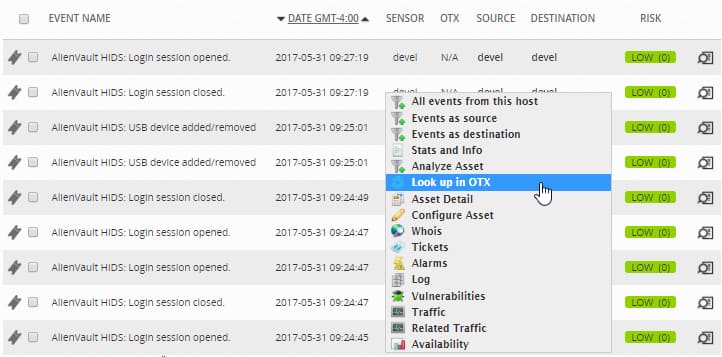 For example, the Look up in OTX option opens the OTX site to display potential and reported threats related to the selected location. If no threat information is found about the location, the Look Up in OTX option opens the Create New Pulse web page in OTX, which lets you create a new Pulse to report a possible new threat.
Sheriff Vigilante Limitations: Although Sheriff Vigilante has a complete integration of OTX in its environment, the additional alarm context compiled by the AT&T Alien Labs™ Security Research Team to analyze and validate OTX threat data is only available in Sheriff CSM.
For example, the Look up in OTX option opens the OTX site to display potential and reported threats related to the selected location. If no threat information is found about the location, the Look Up in OTX option opens the Create New Pulse web page in OTX, which lets you create a new Pulse to report a possible new threat.
Sheriff Vigilante Limitations: Although Sheriff Vigilante has a complete integration of OTX in its environment, the additional alarm context compiled by the AT&T Alien Labs™ Security Research Team to analyze and validate OTX threat data is only available in Sheriff CSM.
