You are here: Docs>Sheriff Web>UserGuides>SheriffCSMDocumentation>UserGuide>EventManagement>SheriffCSMEventProcessingWorkflowEM (10 Sep 2021, SheriffCyberSecurity)Edit Attach
Up
Previous Next Sheriff CSM™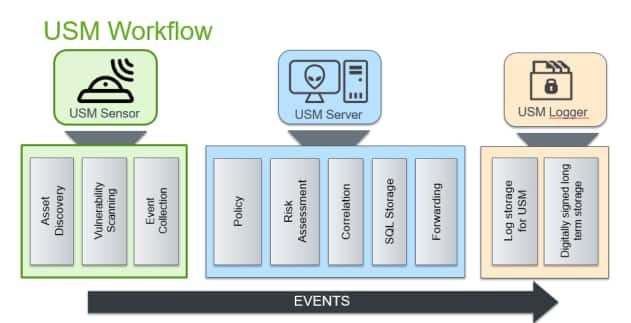 The Sheriff CSM Sensor combines asset discovery, vulnerability assessment, threat detection, and behavioral monitoring to provide full situational awareness. The Sheriff CSM Sensor is the front-line security module of the Sheriff CSM platform and provides detailed visibility into your environment, vulnerabilities, attack targets and vectors, and services.
The Sheriff CSM Sensor normalizes raw log data and other activity or status information from devices into a standardized Sheriff CSM event format. These normalized events are then sent to the Sheriff CSM Server component.
The Sheriff CSM Server provides a unified management interface through the Sheriff CSM web UI that combines security automation, and OTX and AT&T Alien Labs™ Threat Intelligence to correlate data, spot anomalies, reduce risk, and improve operational efficiency.
The Sheriff CSM Server receives events from the Sheriff CSM Sensor and performs policy evaluation. The policy defines what will happen with events. By default, the events are sent to the correlation engine, from the risk assessment module, and then stored in an internal SQL database. Events can also be forwarded to another Sheriff CSM Server, if required. This flow is completely configurable using Sheriff CSM policies.
Correlation can be done logically, where events can be compared to patterns and multiple conditions can be connected by using logical operators such as OR and AND. Correlation can also be calculated using cross-correlation, where events are correlated with vulnerability data. After events are processed and correlated, the Sheriff CSM Server performs risk analyses and triggers an alarm if the risk of the event is high enough.
The Sheriff CSM Sensor combines asset discovery, vulnerability assessment, threat detection, and behavioral monitoring to provide full situational awareness. The Sheriff CSM Sensor is the front-line security module of the Sheriff CSM platform and provides detailed visibility into your environment, vulnerabilities, attack targets and vectors, and services.
The Sheriff CSM Sensor normalizes raw log data and other activity or status information from devices into a standardized Sheriff CSM event format. These normalized events are then sent to the Sheriff CSM Server component.
The Sheriff CSM Server provides a unified management interface through the Sheriff CSM web UI that combines security automation, and OTX and AT&T Alien Labs™ Threat Intelligence to correlate data, spot anomalies, reduce risk, and improve operational efficiency.
The Sheriff CSM Server receives events from the Sheriff CSM Sensor and performs policy evaluation. The policy defines what will happen with events. By default, the events are sent to the correlation engine, from the risk assessment module, and then stored in an internal SQL database. Events can also be forwarded to another Sheriff CSM Server, if required. This flow is completely configurable using Sheriff CSM policies.
Correlation can be done logically, where events can be compared to patterns and multiple conditions can be connected by using logical operators such as OR and AND. Correlation can also be calculated using cross-correlation, where events are correlated with vulnerability data. After events are processed and correlated, the Sheriff CSM Server performs risk analyses and triggers an alarm if the risk of the event is high enough.
Previous Next Sheriff CSM™
Sheriff CSM Event Processing Workflow
After Sheriff CSM is installed in your environment, events start flowing through the Sheriff CSM system, so you can start gaining visibility into what natural or non-threatening activity is taking place, and what worrisome activity, indicating possible attacks, might be taking place. Sheriff CSM also begins collecting other information about your network and various network devices such as firewalls, routers and switches, servers, and applications. In addition, it is discovering and determining possible vulnerabilities and threats your environment might be susceptible to. The following illustration details a high level view of events and other information from your network environment as it is collected or generated by Sheriff CSM Sensors (Deputies) and delivered to the Sheriff CSM Server for processing. The Sheriff CSM Sensor combines asset discovery, vulnerability assessment, threat detection, and behavioral monitoring to provide full situational awareness. The Sheriff CSM Sensor is the front-line security module of the Sheriff CSM platform and provides detailed visibility into your environment, vulnerabilities, attack targets and vectors, and services.
The Sheriff CSM Sensor normalizes raw log data and other activity or status information from devices into a standardized Sheriff CSM event format. These normalized events are then sent to the Sheriff CSM Server component.
The Sheriff CSM Server provides a unified management interface through the Sheriff CSM web UI that combines security automation, and OTX and AT&T Alien Labs™ Threat Intelligence to correlate data, spot anomalies, reduce risk, and improve operational efficiency.
The Sheriff CSM Server receives events from the Sheriff CSM Sensor and performs policy evaluation. The policy defines what will happen with events. By default, the events are sent to the correlation engine, from the risk assessment module, and then stored in an internal SQL database. Events can also be forwarded to another Sheriff CSM Server, if required. This flow is completely configurable using Sheriff CSM policies.
Correlation can be done logically, where events can be compared to patterns and multiple conditions can be connected by using logical operators such as OR and AND. Correlation can also be calculated using cross-correlation, where events are correlated with vulnerability data. After events are processed and correlated, the Sheriff CSM Server performs risk analyses and triggers an alarm if the risk of the event is high enough.
The Sheriff CSM Sensor combines asset discovery, vulnerability assessment, threat detection, and behavioral monitoring to provide full situational awareness. The Sheriff CSM Sensor is the front-line security module of the Sheriff CSM platform and provides detailed visibility into your environment, vulnerabilities, attack targets and vectors, and services.
The Sheriff CSM Sensor normalizes raw log data and other activity or status information from devices into a standardized Sheriff CSM event format. These normalized events are then sent to the Sheriff CSM Server component.
The Sheriff CSM Server provides a unified management interface through the Sheriff CSM web UI that combines security automation, and OTX and AT&T Alien Labs™ Threat Intelligence to correlate data, spot anomalies, reduce risk, and improve operational efficiency.
The Sheriff CSM Server receives events from the Sheriff CSM Sensor and performs policy evaluation. The policy defines what will happen with events. By default, the events are sent to the correlation engine, from the risk assessment module, and then stored in an internal SQL database. Events can also be forwarded to another Sheriff CSM Server, if required. This flow is completely configurable using Sheriff CSM policies.
Correlation can be done logically, where events can be compared to patterns and multiple conditions can be connected by using logical operators such as OR and AND. Correlation can also be calculated using cross-correlation, where events are correlated with vulnerability data. After events are processed and correlated, the Sheriff CSM Server performs risk analyses and triggers an alarm if the risk of the event is high enough. Edit | Attach | Print version | History: r6 < r5 < r4 < r3 | Backlinks | View wiki text | Edit wiki text | More topic actions
Topic revision: r6 - 10 Sep 2021, SheriffCyberSecurity
Copyright 2020 Sheriff Cyber Security, LLC. All rights reserved.
