You are here: Docs>Sheriff Web>UserGuides>SheriffCSMDocumentation>UserGuide>VulnerabilityAssessment>VulnerabilityViews>CurrentVulnerabilitiesAssetVulnerabilityDetails (26 Apr 2022, SheriffCyberSecurity)Edit Attach
Up
Previous Next Sheriff CSM™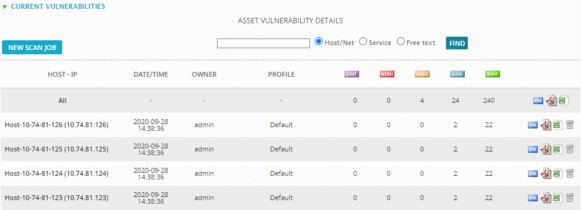 Fields and descriptions for Asset Vulnerability Details
Fields and descriptions for Asset Vulnerability Details
For details about the threshold of vulnerabilities, see Changing the Vulnerability Ticket Threshold.
To filter the data 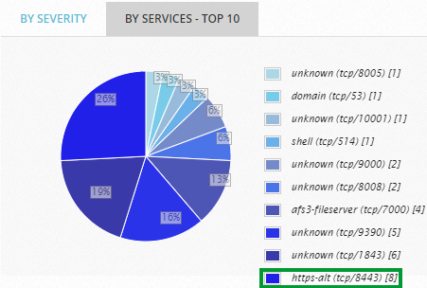 To see which hosts have such vulnerabilities
To see which hosts have such vulnerabilities
Previous Next Sheriff CSM™
Current Vulnerabilities — Asset Vulnerability Details
The Asset Vulnerability Details section summarizes all current vulnerabilities found in the scan jobs by the number of vulnerabilities, in descending order. The first line refers to all scans and the following lines refers to the scans done on every host. Fields and descriptions for Asset Vulnerability Details
Fields and descriptions for Asset Vulnerability Details
| Field | Description |
|---|---|
| Host-IP | Shows the hostname and IP of the host. The first line ‘All’ summarizes all hosts. |
| Date/Time | Shows the exact date and time that the scan occurred. |
| Profile | Indicates the chosen profile to run the scan. |
| Displays the number of Serious vulnerabilities found in the latest scan. | |
| Displays the number of High vulnerabilities found in the latest scan. | |
| Displays the number of Medium vulnerabilities found in the latest scan. | |
| Displays the number of Low vulnerabilities found in the latest scan. | |
| Displays the number of Info vulnerabilities found in the latest scan. | |
| Results of the scan job in HTML within the same browser. | |
| Exports the results of the scan job to a PDF file. The browser, such as Chrome, may open it in a different tab if it recognizes the file extension. | |
| Exports the results of the scan job to an Excel file. | |
| Deletes the report. |
-
In the empty box above the table, enter an IP address of a host/network (default), the name a service, or a free text. Use the following definitions to help you select which one to use:
- Host/Net: Searches the IP address of a single host or a range of IP addresses in a subnet (for example, 10.80.50.73, 10.80.50.1/24).
- Service: Searches the security service identified in the vulnerability (for example, ssh, http, or https, as seen in the By Services -Top 10 pie chart).
- Free text: Searches the details of a vulnerability using free text.
-
Select the corresponding radio button.
-
Click Find.
 To see which hosts have such vulnerabilities
To see which hosts have such vulnerabilities -
Click the text that reads https-alt.
The page refreshes with the text https-alt populated in the search box and the option Service selected.
Only the host(s) with the https-alt vulnerabilities display.
- To check vulnerabilities in details, you can look at the HTML report or export a PDF or Excel file.
Edit | Attach | Print version | History: r17 < r16 < r15 < r14 | Backlinks | View wiki text | Edit wiki text | More topic actions
Topic revision: r17 - 26 Apr 2022, SheriffCyberSecurity
Copyright 2020 Sheriff Cyber Security, LLC. All rights reserved.