Previous Next Sheriff CSM™
About Sheriff CSM System Architecture and Components
As a unified security platform, Sheriff CSM combines several critical security technologies in one integrated platform. Sheriff CSM can be deployed as a single appliance or distributed across multiple servers (either virtual or hardware) to provide additional scalability and availability. The following figure presents a high-level overview of the Sheriff CSM system architecture.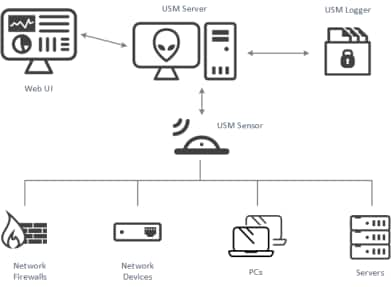 The three components of the Sheriff CSM architecture that work together to monitor and provide security in your environment are
The three components of the Sheriff CSM architecture that work together to monitor and provide security in your environment are -
Sheriff CSM Sensor(s) (Deputy(ies)) — Deployed throughout the network to collect and normalize information from any devices in your network environment that you want to manage with Sheriff CSM. A wide range of plugins are available to process raw logs and data from various types of devices such as firewalls, routers, and host servers.
-
Sheriff CSM Server — Aggregates and correlates information that the Sheriff CSM sensors gather. (This is Sheriff CSM’s SIEM capability.) Provides single pane-of-glass management, reporting, and administration through a web-based user interface.
Basic Sheriff CSM Workflow
There is a consistent workflow that Sheriff CSM follows in collecting raw data from network devices, then parsing and normalizing that data into a stream of events which can then be stored, filtered, and correlated to identify threats and vulnerabilities.-
Sheriff CSM Sensors passively collect logs and mirrored traffic, and actively probe assets in the network, to obtain information about the current network activity going on in your environment.
-
The Sheriff CSM Sensor parses the raw data from different sources and transforms it into a stream of events, each having a common set of data fields. It then sends the events to the Sheriff CSM Server.
-
The Sheriff CSM Server correlates the events and assesses their risk.
- The Sheriff CSM Server sends the events to the Sheriff CSM Logger, which signs them digitally and stores them for forensic analyses, archival, and regulatory compliance.
Sheriff CSM Deployment Options
Sheriff CSM can be deployed in one of two basic configurations:-
Simple Deployment Model — All Sheriff CSM components (Sensor, Server, and Logger) are combined in a Sheriff CSM All-in-One appliance. This configuration is most often used in smaller environments, as well as for demonstrations and proof-of-concept deployments.
- Multi-tier, Distributed Deployment Model — This model deploys each Sheriff CSM component (Sensor, Server, and Logger) as an individual virtual or hardware appliance to create a distributed system topology.
