Previous Next Sheriff CSM™
Policy Consequences
You can configure different consequences when creating or modifying a policy. Policy consequences define the ways in which Sheriff CSM responds to events that trigger the specified policy conditions. You can use consequences to assist you in automatically evaluating elements such as the risk of events, and responding accordingly. Important: When configuring policy consequences, If you change any of the settings in SIEM, Logger, or Forwarding, they will override the default configurations under Configuration > Deployment > Components > Servers. The new consequence configuration will apply to all events that match the policy's conditions.
Actions
Actions are performed when the conditions of the designated policy are met. The default is No Actions. Click the Actions area (green) to display the corresponding section at the bottom of the page. You need to create the actions first before activating them for your policy. See Create an Action for further information.SIEM
The SIEM column displays whether or not SIEM processing is active (Yes), or inactive (No). The default is Yes. Click the SIEM area (green) to display the corresponding section at the bottom of the page. When SIEM processing is set to Yes, you can also modify the individual options.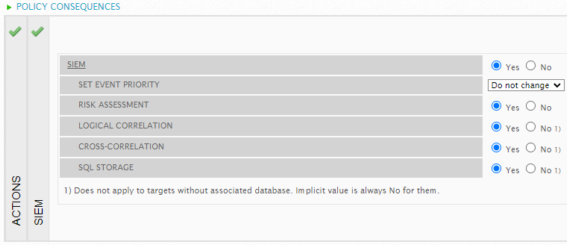
-
Set Event Priority — Changes the priority assigned by Sheriff CSM to events matching the policy conditions, scored from 0-5, with 0 being a non-priority and 5 being the highest importance. The default is Do not change.
Note: Changing the event priority would alter the calculated Risk, therefore turning an event into an alarm, or an alarm into an event.
-
Risk Assessment — Looks at asset value, event priority, and event reliability to evaluate the Risk value of the event. The default is Yes.
-
Logical Correlation — Performs logical correlation as configured in correlation directives. The default is Yes. See also: Correlation Directives.
-
Cross-correlation — Performs cross-correlation related to events. The default is Yes. See also: Cross-Correlation.
-
SQL Storage — Stores events in the SIEM database. The default is Yes.
Forwarding
The Forwarding consequence determines whether to forward events to another Sheriff CSM Server The default is No. By changing the Forwarding consequence to Yes, you can configure all or a subset of events to be forwarded to an alternate server, such as a federated server. For more detailed instructions, see Create a Consequence to Forward Events. Warning: When Forwarding is set to No in a policy consequence, Sheriff CSM will NOT forward the events that match the policy's conditions. This takes precedence over what is configured under Configuration > Deployment > Components > Servers, but only applies to the events that match the policy's conditions. Sheriff Vigilante Limitations: Sheriff CSM includes more robust policies built into the environment, but you are allowed to customize and build your own rules based on your needs in Sheriff Vigilante.Topic revision: 24 Dec 2021, SheriffCyberSecurity