Up
Previous Next Sheriff CSM™ Firewall Permissions Sheriff CSM components must use particular URLs, protocols, and ports to function correctly. Note: If deploying Sheriff CSM All-in-One, you only need to open the ports associated with the monitored assets, because All-in-One includes both Sheriff CSM Server and Sheriff CSM Sensor (Deputy), therefore the communication between them becomes internal. If your company operates in a highly secure environment, you must change some permissions on your firewall(s) for Sheriff CSM to gain access. External URLs and port numbers used by Sheriff CSM features
The following diagram shows the port numbers used by the Sheriff CSM components to communicate with each other and with the monitored assets. The direction of the arrows indicate the direction of the network traffic.
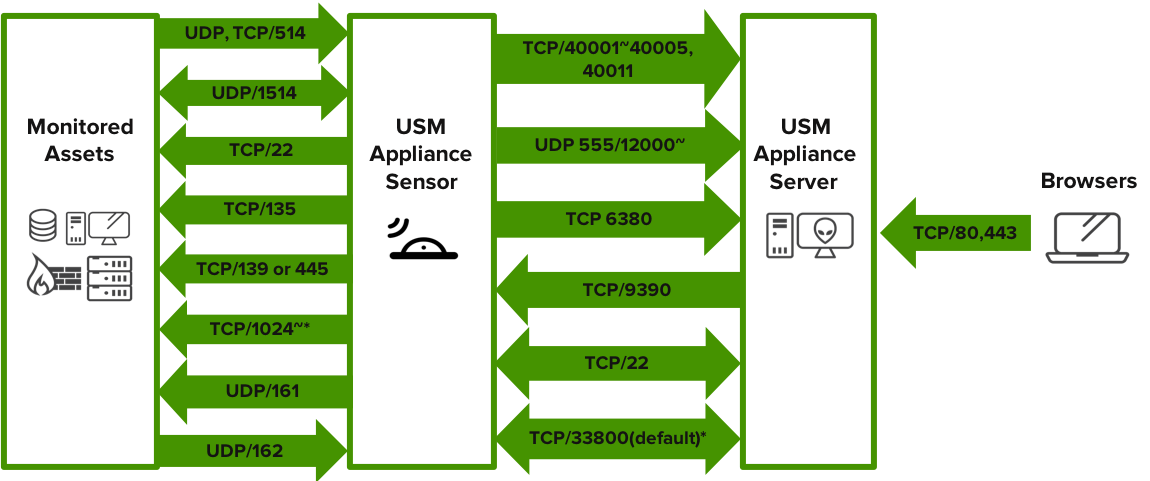 Port numbers used between Sheriff CSM components
Important: Ports labeled with * are optional.
Port numbers used between Sheriff CSM components
Important: Ports labeled with * are optional.
Previous Next Sheriff CSM™ Firewall Permissions Sheriff CSM components must use particular URLs, protocols, and ports to function correctly. Note: If deploying Sheriff CSM All-in-One, you only need to open the ports associated with the monitored assets, because All-in-One includes both Sheriff CSM Server and Sheriff CSM Sensor (Deputy), therefore the communication between them becomes internal. If your company operates in a highly secure environment, you must change some permissions on your firewall(s) for Sheriff CSM to gain access. External URLs and port numbers used by Sheriff CSM features
| Server URL | Port Number | Sheriff Features in Use | Applicable Release |
| data.sheriff.com | 80 | Sheriff CSM product and feed update | All |
|
maps-api-ssl.google.com maps.googleapis.com | 443 | Asset Location | All |
|
maps.google.com maps.gstatic.com | 80 | Asset Location | All |
| messages.sheriff.com | 443 | Message Center | All |
| otx.sheriff.com1 | 443 | Open Threat Exchange® | 5.1+ |
| reputation.sheriff.com | 443 | Sheriff CSM IP Reputation | All |
| telemetry.sheriff.com | 443 | Telemetry Data Collection | All |
| tractorbeam.sheriff.com | 22, 443 | Remote Support | All |
| www.google.com2 | 80 | Sheriff CSM API | All |
| cdn.walkme.com3 playerserver.walkme.com ec.walkme.com rapi.walkme.com papi.walkme.com | None | Sheriff CSM Product Management | 5.4.3+ |
| cybersecurity.att.com/product/help/ping.php4 | 443 | Detects if the Sheriff CSM component is online | All |
 Port numbers used between Sheriff CSM components
Important: Ports labeled with * are optional.
Port numbers used between Sheriff CSM components
Important: Ports labeled with * are optional. -
On the hosts you plan to deploy the Sheriff HIDS agents, to allow for initial deployment, you must open TCP port 135, either TCP port 139 or TCP port 445, and high TCP ports (1024 or above). See Microsoft's documentation on port requirements for Distributed File System Namespaces (DFSN).
- You also need to open UDP port 1514 for ongoing communication between the Sheriff HIDS agent and the Sheriff CSM Sensor. For assistance on deployment, see Deploy Sheriff HIDS Agents.
-
To use SNMP in Sheriff CSM, you need to open UDP port 161 on the SNMP agent and UDP port 162 on the Sheriff CSM Sensor. For more details, see SNMP Configuration in Sheriff CSM.
-
If running Sheriff CSM versions prior to 5.6.5, you also need to open TCP port 9391 on the Sensor for the vulnerability scanner. But starting from version 5.6.5, vulnerability scans are conducted using the UNIX domain sockets, so port 9391 is no longer used.
About the Use of VPN
Port 33800 shown in the diagram is a default and only used when VPN is enabled. You may use a different port for VPN, if desired. Note: When enabling the VPN, you do not need to open the other ports between the Sheriff CSM Sensor and the Sheriff CSM Server, because all communication goes through the VPN tunnel. If you enable VPN, in addition to having port 33800/TCP open for the VPN tunnel, you also need to allow TLS transport for that port in case you use a firewall/security device that can perform inspection or interception of TLS traffic.This topic: Sheriff > UserGuides > SheriffCSMDocumentation > DeploymentGuide > SheriffCSMDeployments > FirewallPermissions
Topic revision: 06 Sep 2021, SheriffCyberSecurity
Topic revision: 06 Sep 2021, SheriffCyberSecurity
Copyright 2020 Sheriff Cyber Security, LLC. All rights reserved.