Up
Previous Next Sheriff CSM™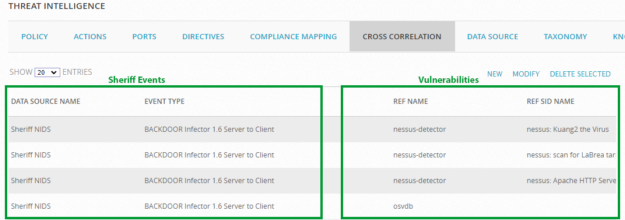 At the bottom of the page, you can navigate to the next pages to see more rules. You can also use the search icon to display the search box, and then search by Data Source Name, Event Type, Ref Name, and Ref SID Name.
At the bottom of the page, you can navigate to the next pages to see more rules. You can also use the search icon to display the search box, and then search by Data Source Name, Event Type, Ref Name, and Ref SID Name.
Previous Next Sheriff CSM™
Cross-Correlation Rules
The correlation engine uses cross-correlation rules to connect NIDS events and vulnerabilities discovered by the Sheriff Vulnerability Scanner. Sheriff CSM provides a web interface, Configuration > Threat Intelligence > Cross Correlation for you to examine, modify, and create cross-correlation rules. At the bottom of the page, you can navigate to the next pages to see more rules. You can also use the search icon to display the search box, and then search by Data Source Name, Event Type, Ref Name, and Ref SID Name.
At the bottom of the page, you can navigate to the next pages to see more rules. You can also use the search icon to display the search box, and then search by Data Source Name, Event Type, Ref Name, and Ref SID Name.

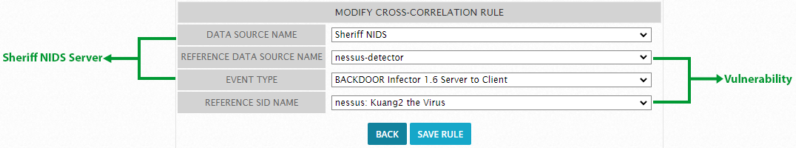
To view a cross-correlation rule, do one of the following
- Double-click the rule.
- Highlight the rule and click Modify.

This topic: Sheriff > UserGuides > SheriffCSMDocumentation > UserGuide > EventCorrelation > CrossCorrelation > CrossCorrelationRules
Topic revision: 05 Jun 2022, SheriffCyberSecurity
Topic revision: 05 Jun 2022, SheriffCyberSecurity
Copyright 2020 Sheriff Cyber Security, LLC. All rights reserved.